In this second part, we will go through the process of Dorking, but most importantly, how data could be searched for within public repositories.
As reminder, Dorking is the ability to find information from searching. Hackers can search through public repositories in order to look for sensitive or confidential details which can be used against you.
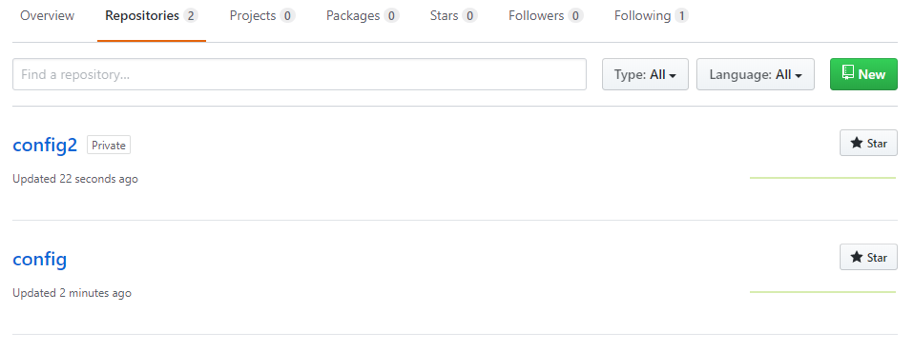
To perform this demonstration, we first create two repositories – one Public and one Private. Then create a file inside each repository to represent a file containing some credentials. However, this will use dummy credentials.
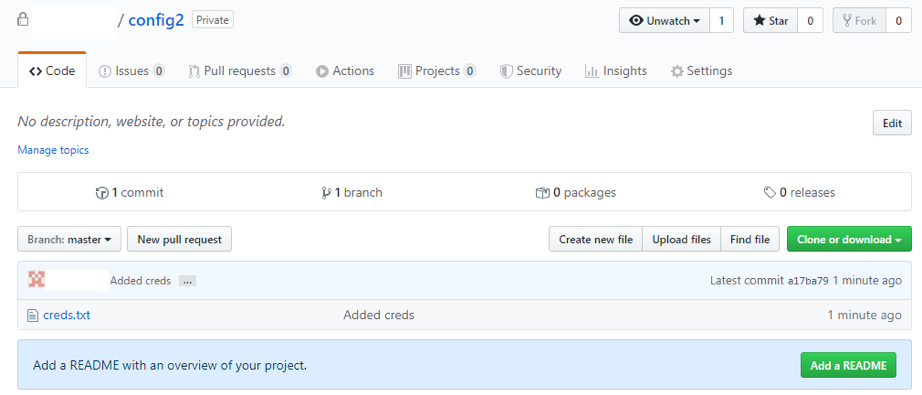
Here are the created repositories:
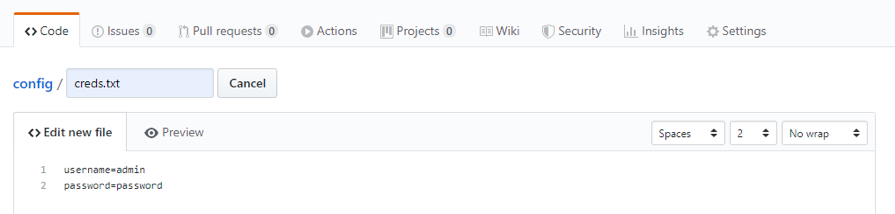
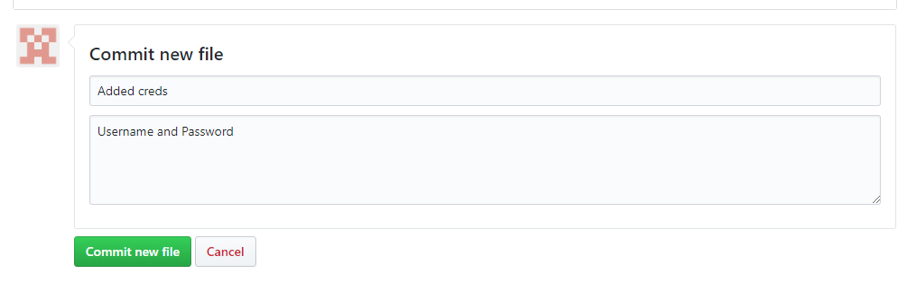
Now we create a file inside each repository with slightly differing dummy credentials. Here is an example for the public config repository. The first screenshot shows adding the credentials and the second shows adding a commit title and description.
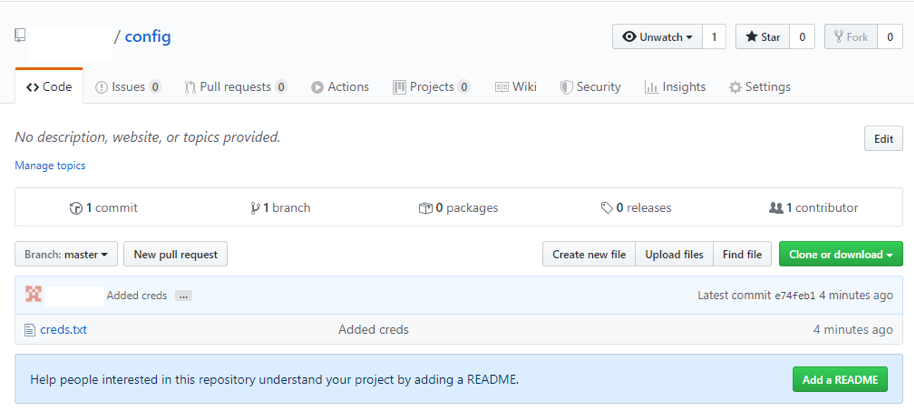
This same process of adding the file to the Public is carried out the Private repository too. In the screen shots below, both Public and Private repositories are set up and ready to use:
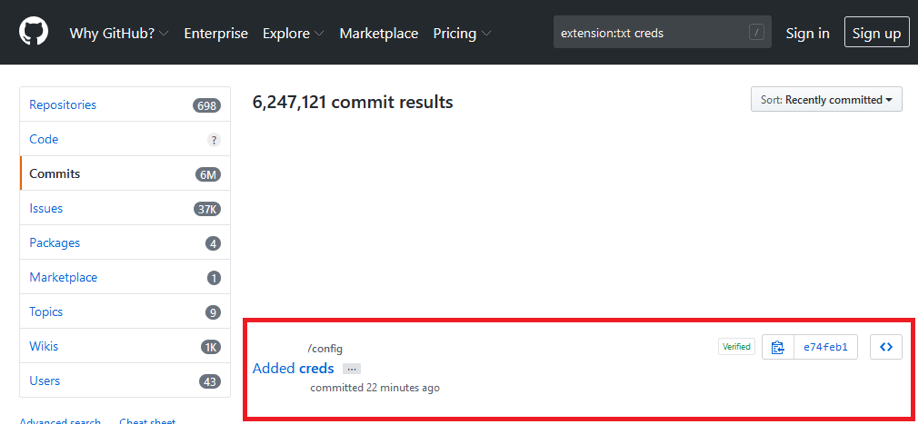
Now the files have been created, and they can be used within the Dorking process. Here, we have specified the extension as txt and then provided ‘creds’ as a search term. It then offers back our public config creds.txt file only.
We can then select the file as usual, and the credentials are displayed, all while not being logged in.
Using the search query “extension:txt creds” the file is found inside the public repository that was created. But we can also do the following which still provides the same except for being on the second page in this case.
Although this was straight forward, the Dorking technique is a powerful tool to find valuable data which may have been leaked.
In the next part of this series we will examine how Dorking can be achieved by using an automated tool.