Continuing from the previous post (Part 1: Android Mobile Penetration Testing), let’s install some important tools. The virtual device is used so that you can test a combination of different versions of android mobile devices and mobile operating systems for vulnerabilities with the tools mentioned in this post.
Android Studio
Download and Install Android SDK from https://developer.android.com/studio
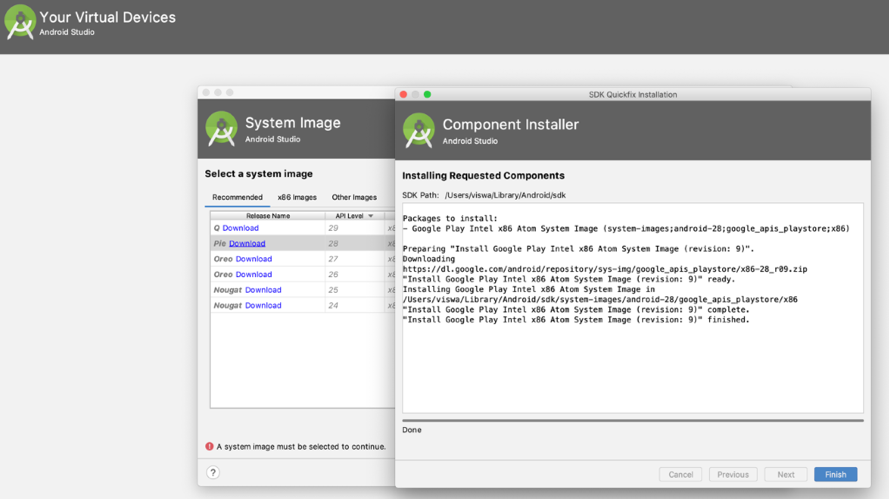
After installation, use Android SDK manager and install at least two of the android platforms (Android 10.0 – Q, Android 9.0 – Pie). Create virtual devices through Android Virtual Device Manager (AVD) Pixel 2 Android 9.0:
Fig:1 Creating Virtual Device
Start the virtual device once installed. It may look different to the below screenshot depending on Android device installed:
Fig:2 Virtual Device Pixel2
Drozer
Download drozer_2.x.x.deb from https://github.com/FSecureLABS/drozer/releases
- Drozer may require other python packages like python-openssl, python-protobuf etc depending on existing Kali or any Linux distro (distributions). Install using apt-get as below:
- apt-get install python-twisted python-openssl python-protobuf
- dpkg -i drozer_2.4.4.deb
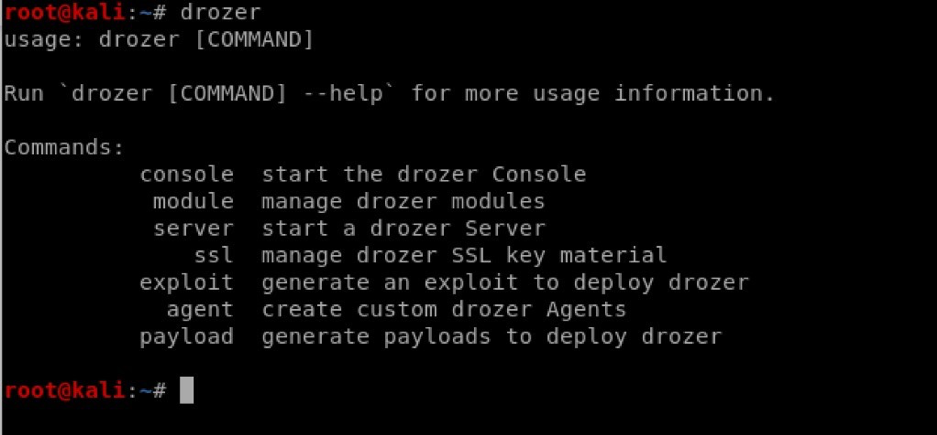
- Run drozer from a command line and verify – output should be as below:
Fig:3 Installing Drozer
Objection (Frida)
This is a Mobile Exploitation tool kit powered by Frida. It helps to assess the Mobile App without the need for Jail broken devices.
Install Objection (Frida) using the below from a command line:
pip3 install -U objection
Sometimes it may take little longer to install with its packages.
Fig:4 Completed Drozer installation
JADX
Install Jadx by downloading from the below Github location:
https://github.com/skylot/jadx/releases
Damn Insecure and Vulnerable App for Android (DIVA)
Download DIVA Mobile App from the below Github location:
https://github.com/payatu/diva-android
How are these Tools related?
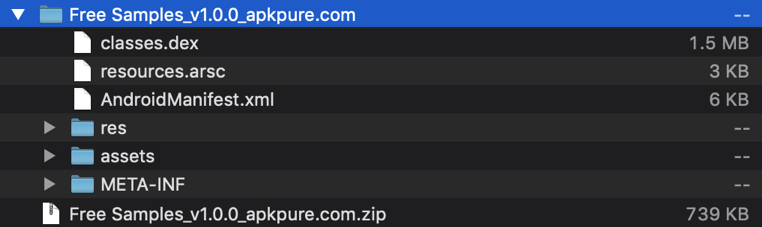
As you may be aware, the Mobile App .apk file is another form of .zip file.
- To extract .apk to source code, rename the .apk file as .zip file.
- Extract the zip file into a directory of choice.
Fig:5 Extrating .apk file
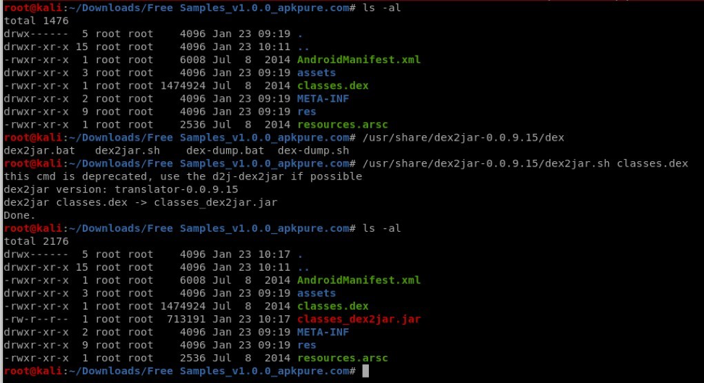
- Convert the extracted classes.dex to .jar using dex2jar:
Fig:6 Converting .dex to .jar
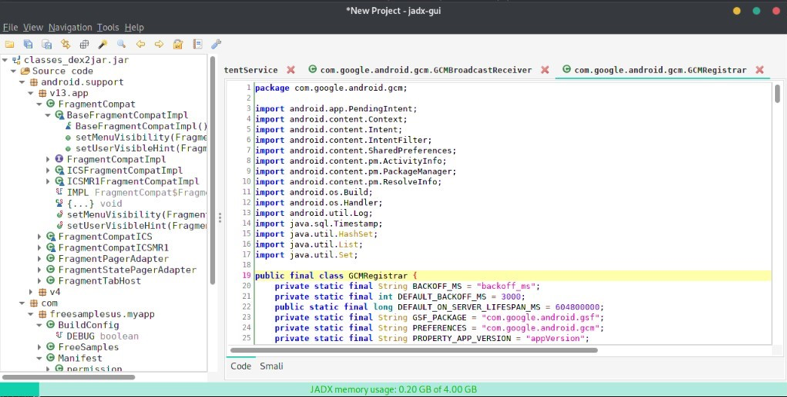
- Run jadx-gui in terminal – the Graphical User Interface (GUI) will then open:
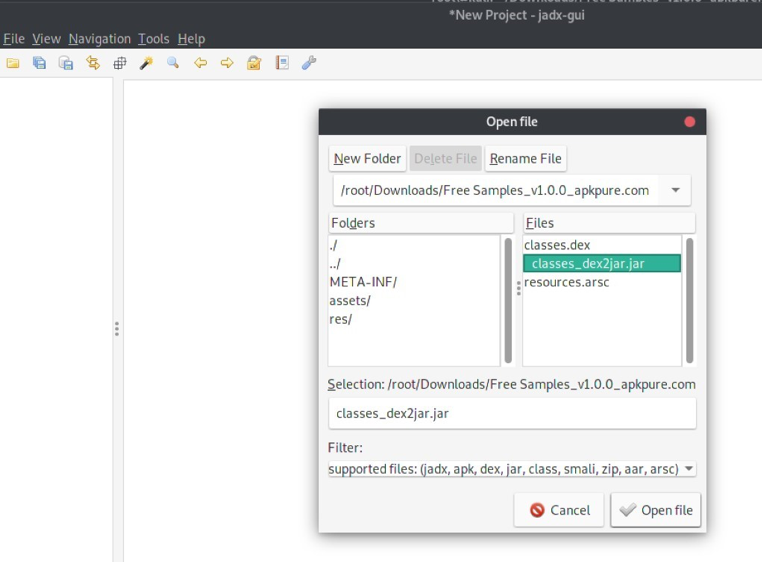
Fig:8 Extracted Source code from jar using Jadx
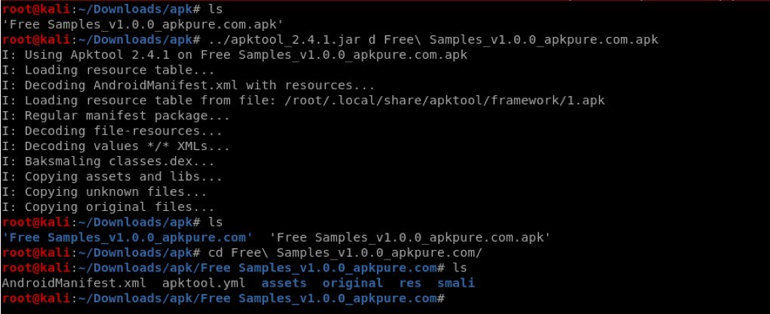
- Alternatively, instead of using the dex2jar and jadx-gui, we can convert the apk to java source code in one step using apktool. This tool can be downloaded from the link https://ibotpeaches.github.io/Apktool/
Fig:9 Extracting Source code from .apk using apktool
Install the Application (apk) into the Virtual Device
Run the below command:
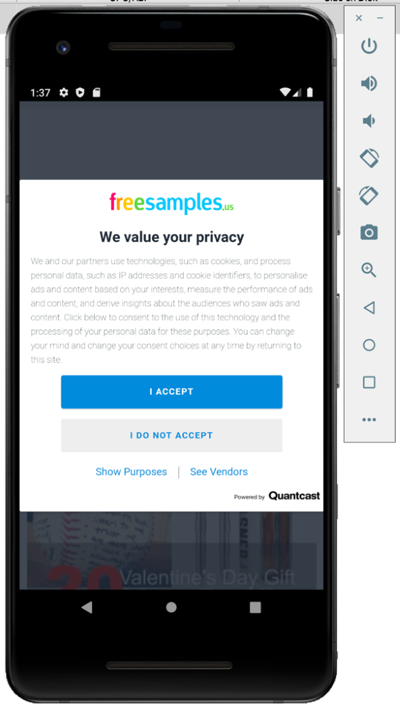
adb -s emulator-5554 install Free\ Samples_v1.0.0_apkpure.com.apk
Now the Free Samples_v1.0.0_apkpure.com.apk into Virtual Device:
Fig:10 After installing App to Virtual Device
We have been focussing on different tools used in Mobile Security testing, its usage and how to install Mobile application into a virtual device in this post. In the coming weeks we will be further looking at different kind of vulnerabilities addressed in Mobile applications.