
This week, we will be looking at Insecure Storage Hardcoded issue and understand its impact on App.

The above screenshots show where the user can enter new 3rd party service username and save their password. This exercise is to show how data can be accessed in an app if stored insecurely. The following data was input for the service username and password – Service username: abp service, service password: password123.
Similar to the previous exercise, click on InsecurityDataStorage1Activity under jakhar.aseem.diva.InsecureDataStorage1Activity class. There are two methods:
- Create
- SaveCredentials
The first method creates the view with edit text and Save button. Once the user enters the 3rd party service username and password, clicking on the ‘Save’ button stores information through the PreferenceManager edit object.
As per Android developer guide, the term PreferenceManager is “used to help create Preference hierarchies from activities or XML.” This suggests the 3rd party username and password is saved somewhere as .xml in the device. Normally this should have been saved in the app path as described in the Android Developer guide. Now we shall attempt to read the .xml stored in the Android emulator. The following are the list of commands/combination to find the location path and read the file:

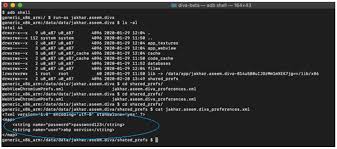
Figure 4: Displays 3rd party username/password
As we have run-as “jakhar.aseem.diva” which is the application package name, the system enables you to read the data related to the app (application). The user credentials are stored in plain text without any hashing algorithms which is not safe.
Remediation:
The app has to use the latest hashing algorithm or preferably to use any encryption technique with Keystore to remain secure.