Part 7: Android Mobile Pen Testing
Part 7: Android Mobile Pen Testing

This week, we will be looking at 2nd Insecure Storage issue and understand its impact on the app.

We can see the 2nd part of the Insecure Data Storage screen looks the same as the previous exercise. The new 3rd party service name and password has been entered and saved (username: root and toor).
Let us inspect the code behind to understand how the data is stored comparing against the previous exercise. Open the classes.dex using jadx gui, click on InsecurityDataStorage2Activity under jakhar.aseem.diva.InsecureDataStorage2Activity class. Here the class InsecurityDataStorage2Activity inherits the properties & methods of AppCompatActivity which is another Android class library. There are two methods available:
- Create
- saveCredentials
The ‘Create’ method declares an object mDB as a private SQLiteDatabase class. An educated guess will lead us possibly to understand that this object will handle DB related actions. Further reading the code we can see the same guess is true. It opens or creates a database based on the name “ids2” this.mDB = openOrCreateDatabase(“ids2”, 0, (SQLiteDatabase.CursorFactory) null);
Then it creates a table “myuser” if the table does not exist and inserts our user input username and password.
| this.mDB.execSQL(“CREATE TABLE IF NOT EXISTS myuser(user VARCHAR, password VARCHAR);”); |
The second method ‘saveCredentials’ takes a parameter of view object which contains the user input username and password and updates the user credentials.
| this.mDB.execSQL(“INSERT INTO myuser VALUES (‘” + ((EditText) findViewById(R.id.ids2Usr)).getText().toString() + “‘, ‘” + ((EditText) findViewById(R.id.ids2Pwd)).getText().toString() + “‘);”); |
Based on exception handling, if no issues, displays user a message “3rd party credentials saved successfully!”. This code walk through has provided ample information that the user’s credentials are stored in database. Let us investigate the database and understand how secure data is stored.
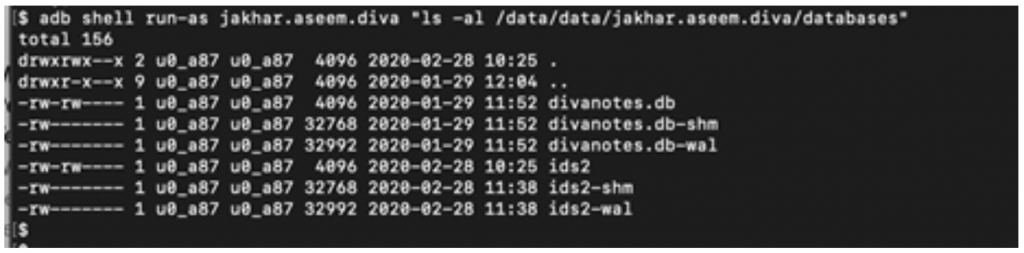
Figure 4 Database Directory listing
As I was not able to directly pull the database file, even though I was running my adb shell as ‘jakhar.aseem.diva’ in an unrooted device, I copied the database ids2 file to an SD card and pulled the database file to a local drive.
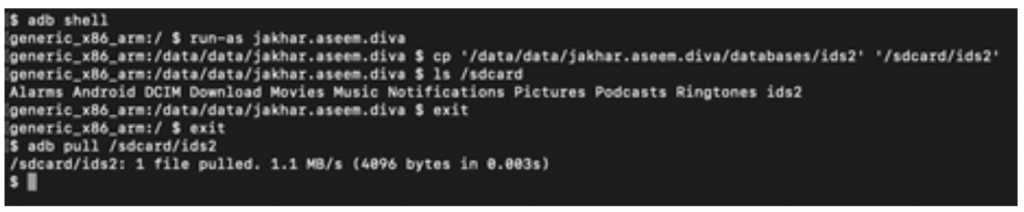
Figure 5 Copying database ids2 to local drive

Open the downloaded database in Sqlite, we can see the myuser table and its value username and password in plain text. This is an InsecureStorage vulnerability where password is stored in plain text.
Remediation
Use any encryption technique with Keystore to store sensitive / confidential data.